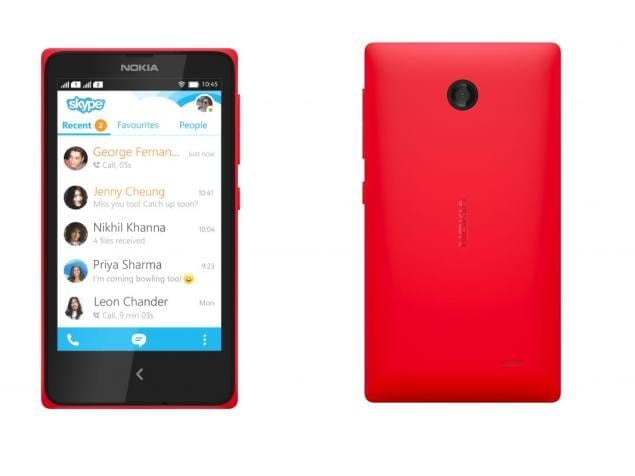
Dell is one of the leading technology inventor.We have heard of Dell's laptops,and now Dell is moving toward inovating tablets. Recently released Dell Venue 8 Pro is something to watch out.
For starters, the Venue 8 Pro has an 8-inch IPS display with 1280x800 resolution, and it packs 32GB of storage. Toshiba’s Encore Mini, for example, is street-priced at just $100, but it has a TN panel that’s limited to 1024x600 resolution and it comes with only 16GB