DNS Changer malware mastermind pleaded guilty

Remember the DNS Changer malware that infected at least four million computers in more than 100 countries, including 500,000 in the United States, with malicious software or malware ? Valeri Aleksejev, 32 years old from Estonia, is the first of the seven individuals to enter a plea, admitting his guilt for his role in the global scam that netted approximately $14 million. He faces up to 25 years in prison, deportation and the forfeiture of $7 million. The other six individuals have been named as Anton Ivanov, Vladimir Tsastsin, Timur Gerassimenko, Dmitri Jegorov, Konstantin Poltev, and Andrey Taame. Alekseev was the first large-scale...
Team GhostShell Exposes 700k accounts from African universities and businesses

The Hacktivist group Team GhostShell today exposes data including 700,000 accounts / records from African universities and businesses during a campaign named ProjectSunRise. Hacker mention, "GhostShell's new project focuses on Africa, mainly, for the time being, South Africa and to some extent other countries from the continent, such as Algeria, Nigeria, Kenya and Angola." In this new campaign hackers have targeted a many companies and universities i.e Angola's National Diamond Corporation, Ornico Marketing, Moolmans Africa Mining Corporation, South African Express Petroleum, State University, Kenyan Business Directory,...
Anonymous hackers deface United States Sentencing Commission website
Anonymous hackers deface the official website of U.S. Sentencing Commission website (ussc.gov) on Friday under a new campaign called "Operation Last Resort" in memory of Reddit co-founder Aaron Swartz and also threatening to release a massive WikiLeaks-style exposure of sensitive U.S. government secrets. “The time has come to show the United States Department of Justice and its affiliates the true meaning of infiltration. The time has come to give this system a taste of its own medicine.” hackers said. The hack was performed in opposition to alleged unjust policies of the United States Department of Justice (DOJ) with the late...
Turkmenistan Gmail, Microsoft, Youtube Domains Hijacked

Iranian hackers deface multiple big companies Turkmenistan domains (.tm) yesterday using DNS poisoning attack. All hacked domains are registered by NIC at Turkmenistan. Hacker managed to find and exploit a SQL Injection vulnerability in NIC website in order to get database of the site. Because the passwords was stored in plain text, that make more easy for those hacker to access the domain panels of each domain and changing the DNS entries to shift websites on a rouge server with defaced page. The defaced message as shown below: Defaced domains : www.youtube.tm www.gmail.tm www.msdn.tm www.intel.tm www.officexp.tm www.xbox.tm www.windowsvista.tm www.orkut.tm www.google.tm Mirror...
I hack, reflection on the role of hacker

The role of hacker is recognized as crucial today in cyber security, these specialists are the nightmare of security experts but their knowledge is fundamental to understand the vulnerabilities of our infrastructures … think like a hacker if you want really protect your system. But hacking is a culture, a way of life that is hard to match ago with the business logic, true hackers don’t do this for money, money are fundamental but not all, the must for them is always to put into question their capabilities, try to consistently exceed their limits. Fortunately industry, private business and governments have understood it and have re-evaluated...
Take down of fifth most widespread 'Virut Botnet'

NASK the domain registrar that operates the “.pl” Polish top-level domain registry has seized multiple domains used for cyber crime activities by spreading Waledac malware distributed by the Virut botnet. According to Poland’s Computer Emergency Response Team, Virut was first detected in 2006 and became a serious threat with an estimated size of more than 300,000 compromised computers. NASK said that on Thursday it began assuming control over 23 .pl domains that were being used to operate the Virut network. Virut was responsible for 5.5% of infections in Q3 2012, making it the fifth most widespread threat of the time. They...
Shylock banking malware spreads via Skype

The banking Trojan known as Shylock has been updated with new functionality, including the ability to spread over Skype. The program was discovered in 2011 that steals online banking credentials and other financial information from infected computers. Shylock, named after a character from Shakespeare's "The Merchant of Venice". Shylock is one of the most advanced Trojans currently being used in attacks against home banking systems. The code is constantly being updated and new features are added regularly. According to security researchers from CSIS Security Group, the Skype infection is based on...
New Java exploit sells for $5000 on Black market

We continues to recommend users disable the Java program in their Web browsers, because it remains vulnerable to attacks that could result in identity theft and other cyber crimes and less than 24 hours after Oracle Sunday released a security update that addresses two critical zero-day vulnerabilities in Java that are being actively exploited by attackers, an online vulnerability seller began offering a brand-new Java bug for sale. According to a report, a Java exploits was being advertised for $5,000 a piece in an underground Internet forum and the new zero-day vulnerability was apparently already in at least one attacker's hands. The...
The use of passwords in a technological evolution

Every day we read about an incredible number of successful attacks and data breaches that exploited leak of authentication mechanisms practically in every sector. Often also critical control system are exposed on line protected only by a weak password, in many cases the default one of factory settings, wrong behavior related to the human component and absence of input validation makes many applications vulnerable to external attacks. Today I desire to focus the attention of a report published by the consulting firm's Deloitte titled “Technology, Media & Telecommunications Predictions 2013” that provide a series of technology predictions,...
Malware Infects US Power Plants through USB Drives

The US Department of Homeland Security’s Cyber Emergency Response Team has released a report, which stated that two American electrical power plants were compromised late last year and has identified a number of glaring electronic vulnerabilities. Some unknown malware infected two power plants control systems using unprotected USB drives as an attack vector. The tainted USB drive came in contact with a handful of machines at the power generation facility and investigators found sophisticated malware on two engineering workstations critical to the operation of the control environment. The report did not say if the computers did...
Cisco Linksys routers vulnerable to remote zero-day exploit

A zero-day vulnerability has been discovered in popular Cisco Linksys routers that allows hackers to gain remote root access. Security vendor DefenseCode discovered the flaw and reported it to Cisco months ago and a fix is already on the way. According to Cisco, more than 70 million Linksys routers sold globally. This exploit was successfully tested against a Linksys model WRT54GL router by researchers at security firm DefenseCode who claimed that the latest Linksys firmware 4.30.14 and all previous versions are still vulnerable. It took the team only 12 days to develop an exploit that could be used by hackers to take control...
Oracle Patches Java Zero Day Vulnerability

Oracle delivered an unusual emergency patch to Java's critical Zero Day vulnerability on Sunday to fix a malicious bug that allowed hackers access to users web browsers. Exploits for the previously undisclosed flaw were being hosted in a number of exploit kits and attacks have already been seen in the wild dropping ransomware and assorted other malware. Security Alert CVE-2013-0422 include two vulnerabilities that are remotely executable. Oracle confirmed that the flaws were only present in Java 7 versions and did not impact Java on servers, Java desktop applications, or embedded Java. Java is used in 3 billion machines,...
Arrested 'Happy Hacker' is the ZeuS Botnet Mastermind

Last week, Happy Hacker arrested in Thailand on charges of stealing millions from online bank accounts. According to new reports same hacker alleged as ZeuS Mastermind and used to have the profile of a miscreant nicknamed “bx1,” a hacker fingered by Microsoft before as a major operator of botnets powered by the ZeuS banking trojan. He remained smiling throughout a press conference in which Thai police explained that Thailand will seek to extradite Mr Bendelladj to the US state of Georgia, where a court has issued a warrant for his arrest. 24-year-old Algerian Hacker , Hamza Bendelladj arrested at a Bangkok airport...
Exploit Packs updated with New Java Zero-Day vulnerability
A new Java 0-day vulnerability has been discovered, already wind in use by an exploit pack, taking advantage of a fresh zero-day vulnerability in Java and potentially letting hackers take over users’ machines. Java 7 Update 10 and earlier contain an unspecified vulnerability that can allow a remote, unauthenticated attacker to execute arbitrary code on a vulnerable system. The flaw was first spotted by ‘Malware Don’t Need Coffee’ blog. This vulnerability is being attacked in the wild, and is reported to be incorporated into exploit kits. This exploit is already available in two Exploit Packs, that is available...
Under the hood of recent DDoS Attack on U.S. Banks

Incapsula security study reveals how a simple neglect in managing the administrative password of a small UK site was quickly exploited by Botnet shepherds operating obscurely out of Turkey to hurl large amounts of traffic at American banks. If you've been following the news, you are probably aware of a wave of DDoS attacks that recently hit several major U.S. banks. Izz ad-Din al-Qassam, a hacker group that claimed responsibility for these attacks, declared them to be a retaliation for an anti-Islam video that mocked the Prophet Muhammad and a part of the on-going “Operation Ababil.” As the reports of the attack started...
5 Checks You Must Run To Ensure Your Network Is Secure

Twenty-four hours a day, seven days a week, 365 days each year – it’s happening. Whether you are awake or asleep, in a meeting or on vacation, they are out there probing your network, looking for a way in. A way to exploit you; a way to steal your data, a place to store illegal content, a website they can deface, or any of a hundred other ways to mess with you for the simple joy of it all. And they can do this with relative ease, even in an automated fashion, with simple tools that are readily available to all. I’m talking about network scanners. The bad guys use them all day every day to assess networks around the world because a network...
Outdated version of WordPress leads to MasterCard Hack

On tip of a readers, yesterday we came across a new MasterCard hack, performed by Syrian Electronic Army. Hackers was able to breach MasterCard Blog (https://insights.mastercard.com) and make a new blog post on the website with title "Hacked By Syrian Electronic Army" on January 5, 2013. For now MasterCard deleted that post, but readers can check Google cache. Today we tried to contact the hacker, but may be they are busy in Hacking Next Target , I started my investigation that how they can hack such a big economic website's blog. Starting from very first step, Information gathering about your target. Simple by...
Official Debian and Python Wiki Servers Compromised

Administration from Debian and Python project official websites confirmed that their WIKI servers were compromised by some unknown hackers recently. Hackers was able to hack because of several vulnerabilities in "moin" package. According to Brian Curtin at Python Project, Hacker user some unknown remote code exploit on Python Wiki server (http://wiki.python.org/) and was able to get shell access. The shell was restricted to "moin" user permissions, where but no other services were affected. Attacker deleted all files owned by the "moin" user, including all instance data for both the Python and Jython wikis. Python...
Running Desktop Apps on Windows RT, The Hackers Way!

A hacker claims to have found a method in the code integrity mechanism in Windows RT, that allow one to bypass security mechanism preventing unauthorized software running on ARM-powered Windows RT tablets. Lets see, How to Run traditional desktop apps on Windows RT in a Hackers Way! A hacker called 'C. L. Rokr' explain about the Windows RT exploit on his blog, which requires manipulating a part of Windows RT's system memory that governs whether unsigned apps can run. Windows RT is a special version of Microsoft Windows designed for lightweight PCs and tablets that are based on the ARM architecture, including Microsoft's...
Hacking Facebook Passwords like changing your own Password
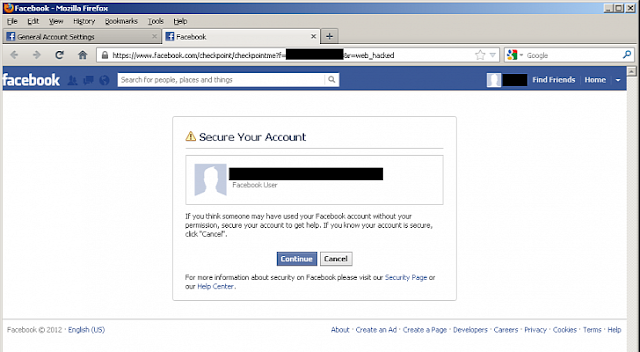
Hacker found a way to hack and change your password like, just he used to change his own password. Confused ? Recently Facebook fix a very critical vulnerability on the tip of 'Sow Ching Shiong', an independent vulnerability researcher. Flaw allows anyone to reset the password of any Facebook user without knowing his last password. At Facebook, there is an option for compromised accounts at "https://www.facebook.com/hacked" , where Facebook ask one to change his password for further protection.
No comments:
Post a Comment